Use context: kubectl config use-context k8s-c1-H
Create a new ServiceAccount processor in Namespace project-hamster. Create a Role and RoleBinding, both named processor as well. These should allow the new SA to only create Secrets and ConfigMaps in that Namespace.
译文:
在namespace project-hamster 中创建一个新的ServiceAccount processor 。创建一个角色和RoleBinding,这两个都是命名的 processor 。这些应该允许新的SA只在该命名空间中创建Secrets和ConfigMaps。
解答:
有4种不同的RBAC组合和3种有效的组合。
- Role + RoleBinding(适用于单一命名空间,适用于单个命名空间)
- ClusterRole + ClusterRoleBinding (全集群可用,适用于整个集群)
- ClusterRole + RoleBinding(全集群可用,适用于单个命名空间)
- Role + ClusterRoleBinding(不可用:在单个命名空间中可用,适用于整个集群)
k config use-context k8s-c1-H创建ServiceAccount,role
k -n project-hamster create sa processor
k -n project-hamster create role processor \
--verb=create \
--resource=secret \
--resource=configmap创建 rolebinding
k -n project-hamster create rolebinding processor \
--role processor \
--serviceaccount project-hamster:processor验证
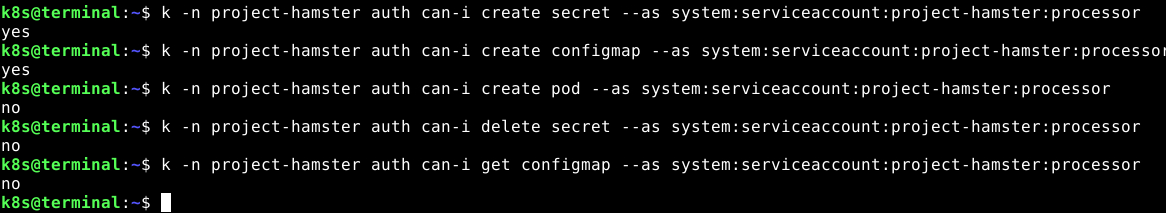
k -n project-hamster auth can-i create secret \
--as system:serviceaccount:project-hamster:processor
k -n project-hamster auth can-i create configmap \
--as system:serviceaccount:project-hamster:processor
k -n project-hamster auth can-i create pod \
--as system:serviceaccount:project-hamster:processor
k -n project-hamster auth can-i delete secret \
--as system:serviceaccount:project-hamster:processor
k -n project-hamster auth can-i get configmap \
--as system:serviceaccount:project-hamster:processor