![]()
端口扫描
nmap 10.129.171.69
nmap 10.129.171.69 -A -p 21,80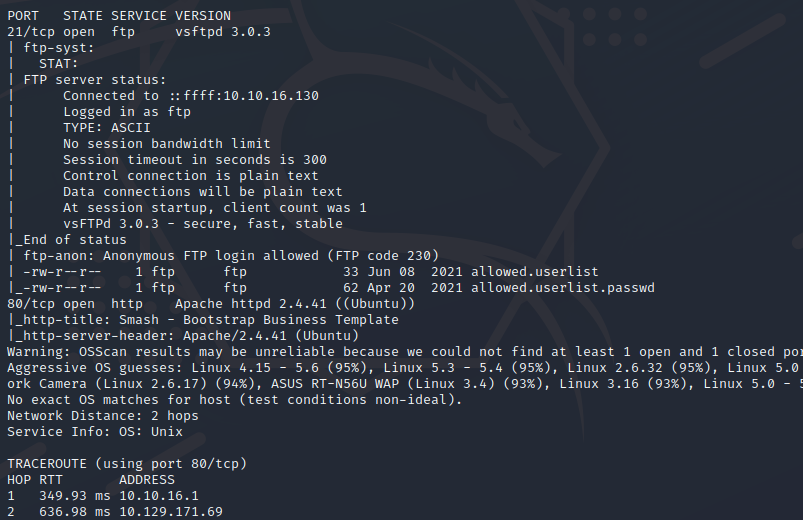
允许匿名用户登录, 并且存在两个文件
ftp 10.129.171.69
Anonymous #登录
ls #列出目录
get allowed.userlist
get allowed.userlist.passwd
exit
cat allowed.userlist
cat allowed.userlist.passwd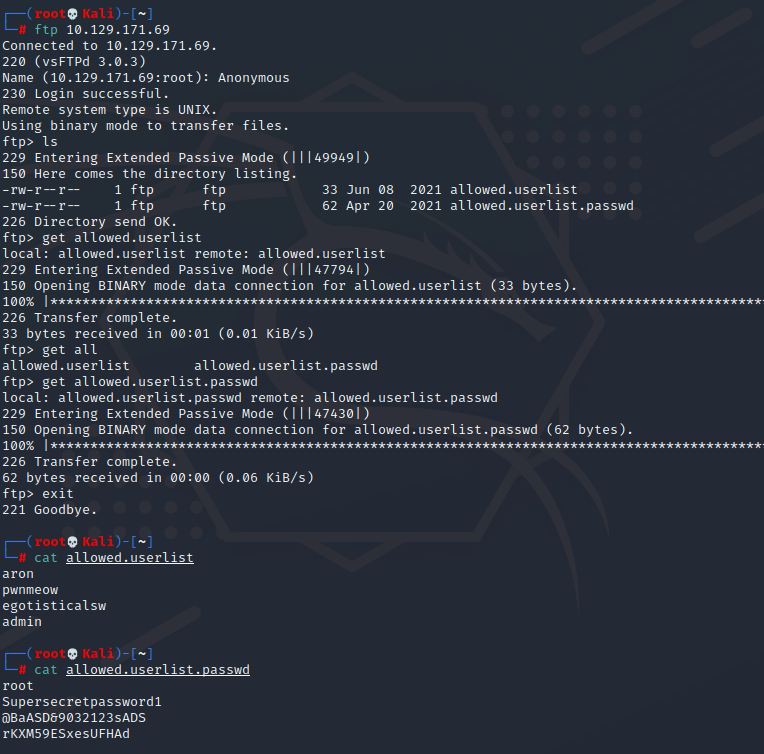
浏览80端口
爆破路径
gobuster dir -u 10.129.171.69 -w /usr/share/dirbuster/wordlists/directory-list-2.3-small.txt -x .php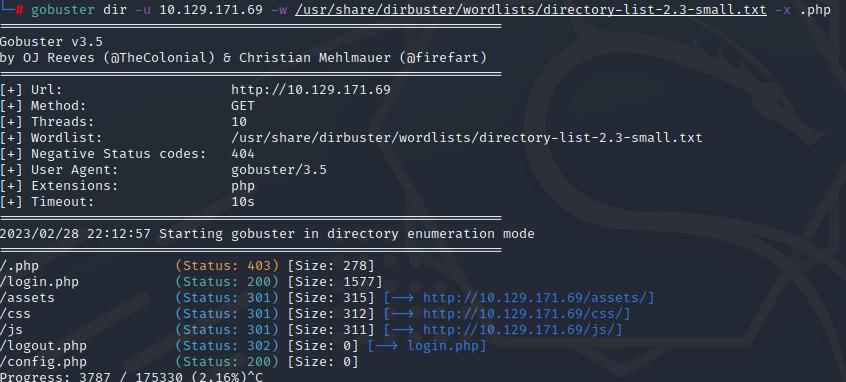
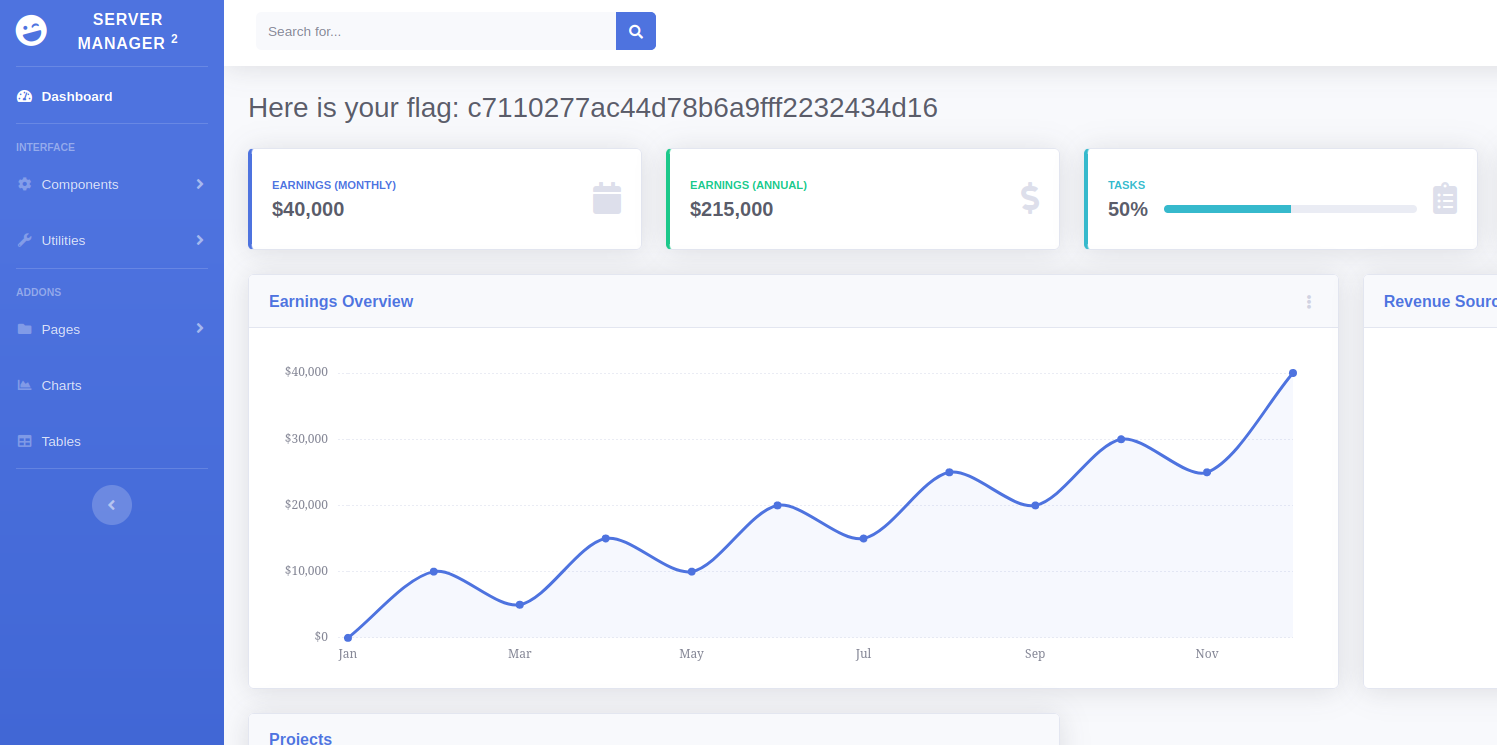
用上面文件的信息登录下,获得flag
-
Task 1 What Nmap scanning switch employs the use of default scripts during a scan?
-sC -
Task 2 What service version is found to be running on port 21?
vsftpd 3.0.3 -
Task 3 What FTP code is returned to us for the "Anonymous FTP login allowed" message?
230 -
Task 4 After connecting to the FTP server using the ftp client, what username do we provide when prompted to log in anonymously?
Anonymous -
Task 5 After connecting to the FTP server anonymously, what command can we use to download the files we find on the FTP server?
get -
Task 6 What is one of the higher-privilege sounding usernames in 'allowed.userlist' that we download from the FTP server?
admin -
Task 7 What version of Apache HTTP Server is running on the target host?
Apache httpd 2.4.41 -
Task 8 What switch can we use with Gobuster to specify we are looking for specific filetypes?
-x -
Task 9 Which PHP file can we identify with directory brute force that will provide the opportunity to authenticate to the web service?
login.php
