Task weight: 9%
Use context: kubectl config use-context k8s-c1-H
There was a security incident where an intruder was able to access the whole cluster from a single hacked backend Pod.
To prevent this create a NetworkPolicy called np-backend in Namespace project-snake . It should allow the *backend-** Pods only to:
connect to *db1-*** Pods on port 1111 connect to db2-**** Pods on port 2222 Use the app label of Pods in your policy.
After implementation, connections from *backend-*** Pods to vault-**** Pods on port 3333 should for example no longer work.
译文:
曾经发生过一起安全事件,一个入侵者能够从一个被入侵的后端Pod访问整个集群。
为了防止这种情况,在 namespace project-snake 中创建一个名为 np-backend 的NetworkPolicy。它应该只允许 *backend-** Pods进入。
- 连接到1111端口的db1-* Pods
- 连接到2222端口的db2-* Pods。
在你的策略中使用Pods的 app 标签。
实施后,例如,从 *backend-*** Pods到3333端口的 vault-**** Pods的连接应该不再工作。
解答:
kubectl config use-context k8s-c1-H查看pod详情
k -n project-snake get pod
k -n project-snake get pod -L app
k -n project-snake get pod -o wide
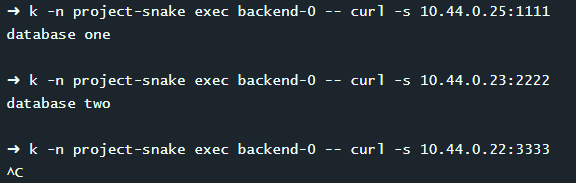
k -n project-snake exec backend-0 -- curl -s 10.44.0.25:1111
k -n project-snake exec backend-0 -- curl -s 10.44.0.23:2222
k -n project-snake exec backend-0 -- curl -s 10.44.0.22:3333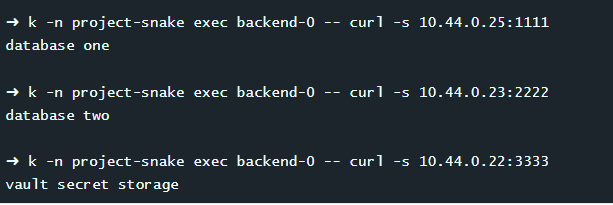
vim 24.yaml24.yaml
# 24_np.yaml
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: np-backend
namespace: project-snake
spec:
podSelector:
matchLabels:
app: backend
policyTypes:
- Egress # policy is only about Egress
egress:
- # first rule
to: # first condition "to"
- podSelector:
matchLabels:
app: db1
ports: # second condition "port"
- protocol: TCP
port: 1111
- # second rule
to: # first condition "to"
- podSelector:
matchLabels:
app: db2
ports: # second condition "port"
- protocol: TCP
port: 2222创建networpolicy
k -f 24.yaml create验证测试
k -n project-snake exec backend-0 -- curl -s 10.44.0.25:1111
k -n project-snake exec backend-0 -- curl -s 10.44.0.23:2222
k -n project-snake exec backend-0 -- curl -s 10.44.0.22:3333