Task weight: 2%
Use context: kubectl config use-context k8s-c2-AC
Node cluster2-node1 has been added to the cluster using kubeadm and TLS bootstrapping.
Find the "Issuer" and "Extended Key Usage" values of the cluster2-node1:
kubelet client certificate, the one used for outgoing connections to the kube-apiserver. kubelet server certificate, the one used for incoming connections from the kube-apiserver. Write the information into file /opt/course/23/certificate-info.txt .
Compare the "Issuer" and "Extended Key Usage" fields of both certificates and make sense of these.
译文:
节点 cluster2-node1 已经使用kubeadm和TLS引导添加到集群中。
找到cluster2-node1的 "Issuer "和 "Extended Key Usage "值。
kubelet客户端证书,用于向外连接kube-apiserver。 kubelet服务器证书,用于从kube-apiserver传入的连接。 将这些信息写入文件 /opt/course/23/certificate-info.txt 。
比较两个证书的 "Issuer "和 "Extended Key Usage"字段,并对这些内容进行理解。
解答:
参考: https://kubernetes.io/zh-cn/docs/reference/command-line-tools-reference/kubelet/
kubectl config use-context k8s-c2-AC远程到cluster2-node1节点,使用openssl进行查看
ssh cluster2-node1
#client证书
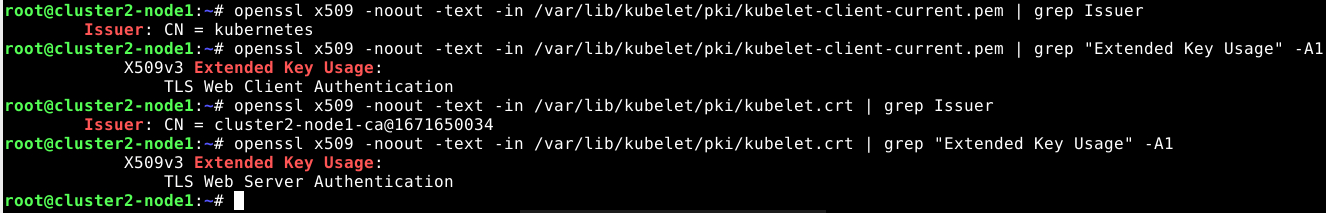
root@cluster2-node1:~# openssl x509 -noout -text -in /var/lib/kubelet/pki/kubelet-client-current.pem | grep Issuer
root@cluster2-node1:~# openssl x509 -noout -text -in /var/lib/kubelet/pki/kubelet-client-current.pem | grep "Extended Key Usage" -A1
#server证书
root@cluster2-node1:~# openssl x509 -noout -text -in /var/lib/kubelet/pki/kubelet.crt | grep Issuer
root@cluster2-node1:~# openssl x509 -noout -text -in /var/lib/kubelet/pki/kubelet.crt | grep "Extended Key Usage" -A1